Ponemon Institute. (2016). Cost of data breach study: Global analysis. Retrieved December 8, 2018, from https://www-01.ibm.com/marketing/iwm/dre/signup?source = mrs-form-1995&S_PKG = ov49542
Public Company Accounting Oversight Board (2OB). (2010). Identifying and assessing risks of material misstatement. AS No. 12.
Public Company Accounting Oversight Board (PCAOB). (2013). Considerations for audits of internal control over
financial reporting.
Public Company Accounting Oversight Board (PCAOB). (2014). Auditing standard no. 2 - An audit of internal control
over financial reporting performed in conjunction with an audit of financial statements
Bernard, T. S., Hsu, T., Perlroth, N., & Lieber, R. (2017). Equifax Says Cyberattack May Have Affected 143 Mil-
lion in the U.S.. New York Times (September 7, 2018). Retrieved December 8, 2018, from https://www.nytimes. com/2017/09/07/business/equifax-cyberattack.html
Pierangelo Rosati , Fabian Gogolin & Theo Lynn (2020): Cyber-Security Incidents and Audit Quality, European Accounting Review
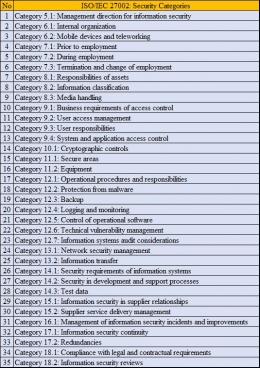
International Standardization Organization - ISO. (2013). International Standard ISO/IEC 27002: Information technology - Security techniques - code of practice for information security controls (2nd ed.). International Standardization Organization - ISO.
International Standardization Organization - ISO. (2013). International Standard ISO/IEC 27002: Information technology - Security techniques - Information security management systems - Requirements (2nd ed.). International Standardization Organization - ISO.
ISACA. (2010). Information Security Management Audit/Assurance Program. Retrieved from www.isaca.org ISACA. (2014).
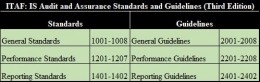
ITAF 3rd Edition: A Professional Practices Framework for IS Audit/Assurance. Retrieved from www.isaca.org
ISACA. (2017). Auditing Cyber Security: Evaluating Risk and Auditing Controls. Retrieved from www.isaca.org